AWS Custom VPC
I wanted to launch & connect my EC2 instance to AWS RDS via terraform. So, I followed the documentation and
- created my own VPC
- security groups, EBS volume, then
- launched EC2
I was able to do SSH and started working on creating AWS RDS terraform script to launch it and connect to it. So I started reading blogs, post and watched some videos so I can perform my task successfully.
In every blog, video and post they were creating subnets, internet gateways, route tables in addition to what I currently have in my script. Then I went to AWS console to check my security group’s VPC and it was under default VPC provided by AWS. But why?
The reason was while creating security groups I haven’t mentioned the vpc_id. So I did that and then new error occurred i.e. my EC2 instance was not able to find the security group. Then I got know that while creating our own VPC I have to pass security group using different keyword called vpc_security_group_ids instead of security_groups.
Again I corrected the same and again a error occurred i.e. security groups do not contain this subnet_id.
The Beginning
Due to simultaneous errors, I went straight to learn the network flow of AWS. What is a VPC, how it connects to outside world, subnets, routes tables and other stuff.
So, I will explain the terminologies and what I understood from this.
- default AWS VPC comes preconfigured that is able to connect to outside world.
- A custom VPC is a private VPC that means no public interface, so there is no outside world access to services that comes under this VPC. A CIDR(IP) range is provided to VPC by user. For example 10.0.0.0/16 range has provided that means 65,536 IPs are available under this VPC.
- Subnet: Subnet is a subset of CIDR range of VPC that is X number of IP available allocated from IP range available to VPC. For example, 10.0.1.0/24 means 256 IPs are available in this subnet. But why Subnet are needed? Answer — to differentiate which service is able to connect to outside world and which are not.
- Internet Gateway(IG): It allows a range of IPs to connect to outside world. But how to decide which IP range? That is done by route tables.
- Route tables attach internet gateway to one or more subnets of a VPC. If IG is attached to a subnet then it is called public subnet else private subnet.
- Security groups: It is a set of protocols that tell from which IP and port a AWS service is available. You can say it is a firewall rules for your system. If port 22 is open then you can SSH to your instance else even if machine is launched successfully you would not be able to login to instance.
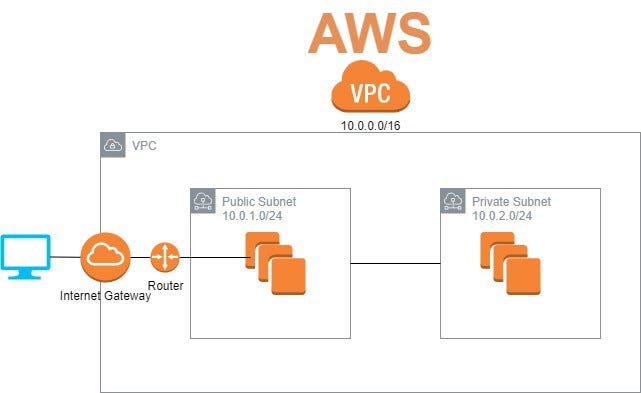
The Above Image
- VPC has given a CIDR range of 10.0.0.0/16
- Then a internet gateway is created that would ask for VPC name while creation.
- There are two service for example i) EC2 Instance ii) RDS database, So I don’t want my database goes public but EC2 instance should have access to outside world.
- So, for isolation for this condition two subnets were created i)10.0.1.0/24 ii) 10.0.2.0/24 and tried to attach first subnet to IG.
- So, for routing the outside world traffic to first subnet, a route table was created that can work as router. A route table asks for one or more subnets & internet gateway(optional). So, the first subnet is attached to this IG through route table.
- Another route table was created to internally route the traffic from EC2 instance to RDS database(queries) and in this case IG was not attached hence a private router and a private subnets.
Thanks for reading!!!

